To know more about KeyPoint or to register your interest in using it,
please contact us: keypoint@qcif.edu.au
KeyPoint is an eResearch platform that enables data custodians/stewards to manage and share sensitive research data with approved researchers in a scalable, fully governed, and highly secure environment, whilst maintaining full control of their data at all times.
Having been co-designed with researchers responsible for valuable data assets with a broad range of stringent data governance and analysis requirements, KeyPoint comprises all the infrastructure, software, systems and analytical tools required by researchers to conduct powerful data analyses on authorised data to address their research questions.
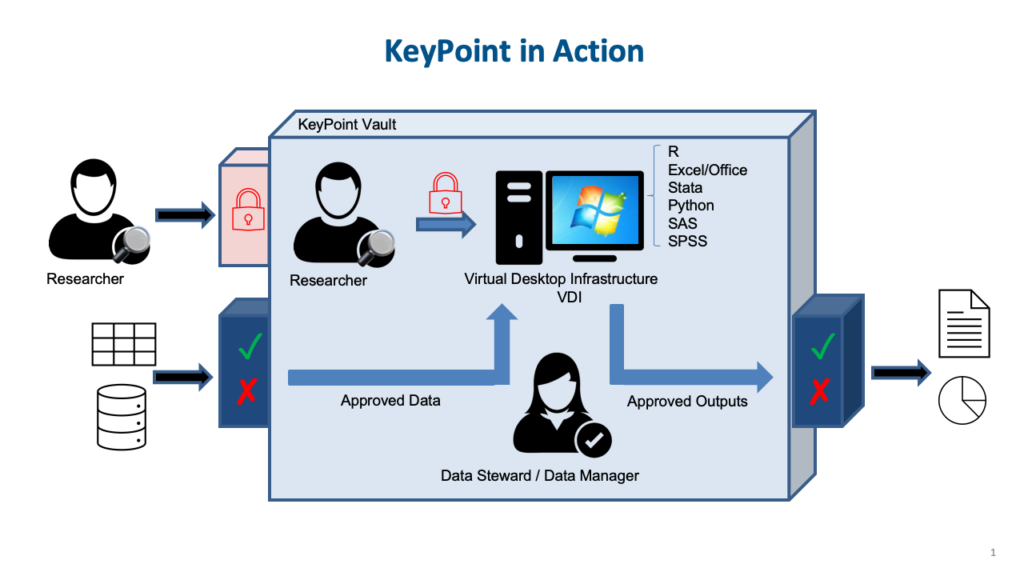
Each project has its own self-contained and self-managed workspace, called a Vault. Each Vault contains their datasets that are being made available for specific research purposes. Each Vault contains strongly separated research activities. Each Research Activity encompasses the datasets (or specific slices of the datasets) that have been shared to it, the set of researchers granted access to the Research Activity, and its own storage space to facilitate collaboration. Further, each Researcher has their own personal storage space for their work, which is specific to a Research Activity.
Access to the entire environment uses the Australian Access Federation (AAF) and a user’s institutional credentials/login coupled with an additional layer of authentication specific to KeyPoint.
Support for external, non-AAF enabled collaborators is provided through QCIF’s use of AAF’s Virtual Home capability.
All data entering and leaving a Vault in KeyPoint must be approved by the Vault’s Data Steward (or their delegated Data Approvers) under the rules of the project’s data governance requirements:
- The Researcher must make a request to bring additional data into their user drive (ingress) or to download results (egress).
- If approved, the files become available on the User drive (ingress) or can be downloaded (egress).
KeyPoint is being deployed in a separate, restricted access region on the QCIF-managed Queensland node of the ARDC Nectar Research Cloud. KeyPoint’s compute infrastructure provides workstation-scale analytics environments, including high-memory virtual desktops for data-intensive workloads and GPU-enabled virtual desktops for visualisation and/or machine learning and AI workloads.
By using KeyPoint, researchers can gain the required trust to receive sensitive data for analysis from State and Federal Data Custodians.